AD Preparation
1- Extend Active Directory Schema
The Active Directory Schema needs to be extended by two new attributes that store the password of the managed local Administrator account for each computer and the timestamp of password expiration. Both attributes are added to the may-contain attribute set of the computer class.
ms-Mcs-AdmPwd – Stores the password in clear text
ms-Mcs-AdmPwdExpirationTime – Stores the time to reset the password
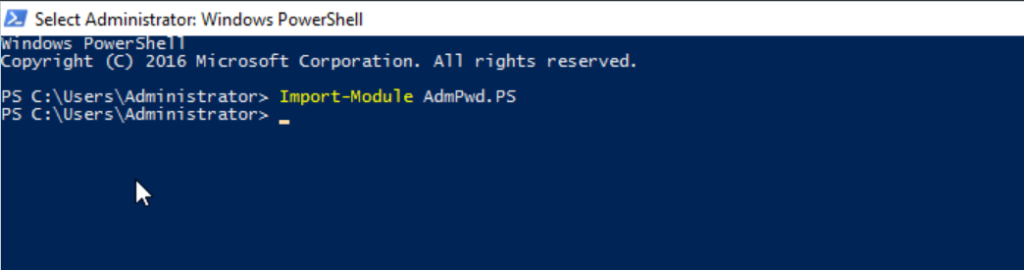
To update the Schema, you first need to import the PowerShell module. Open up an Administrative PowerShell window and use this command:
Import-module AdmPwd.PS
You should update the Schema with this command:
Update-AdmPwdADSchema
If you have Read-Only Domain Controller RODC, check this article Microsoft which explain how you can replicate pwd attributes to read-only domain controllers.
2- Check/Set Permissions to Read Local Admin
On my test network below you can see I’ve got a couple of test Windows Server machines in an OUs called ‘Restricted Computers & Un-Restricted Computers.’
The second thing I need to do is grant the rights to the computers themselves to be able to update the password in Active Directory.
(If you have nested OU’s, only apply on the top level OU).
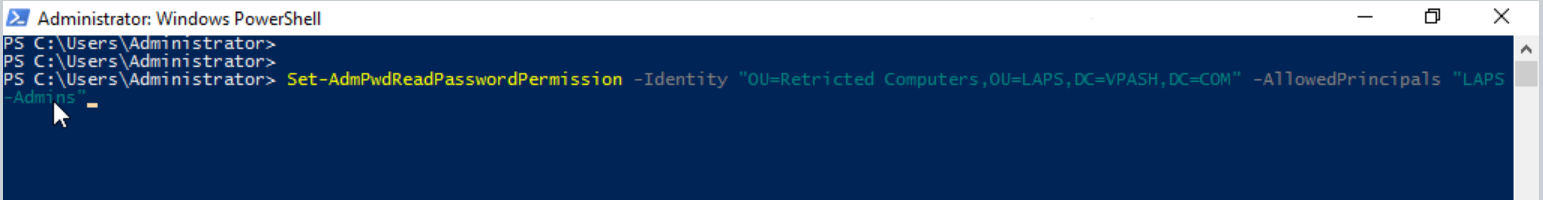
To grant read password permissions to a particular group, use the following syntax, below I have an AD group called LAPS-Admins, and I’m adding it into the AD-ACL to be able to read local administrator passwords for the Restricted Computers OU.
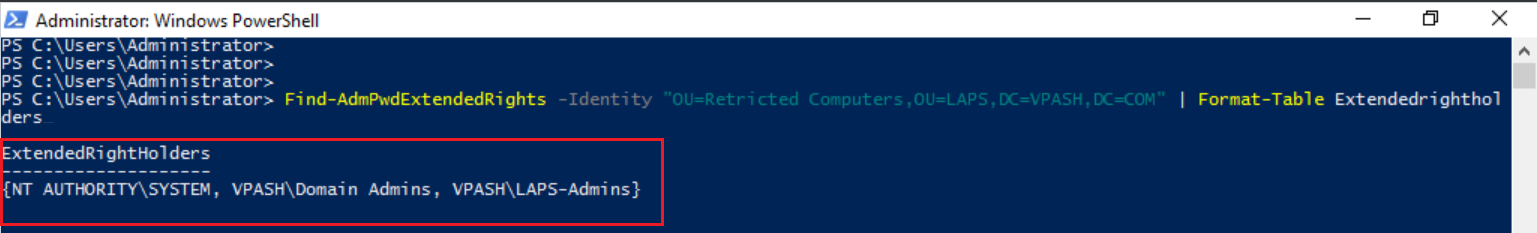
The selected group has been granted as shown below.
3- Deploy the GPO Extensions to ‘Controlled’ Machines.
Then create GPO and link this policy on Restricted Computers org unit, and edit this GPO to enable LAPS policies.
Edit GPO, then going to settings are located under Computer Configuration\Administrative Templates\LAPS.
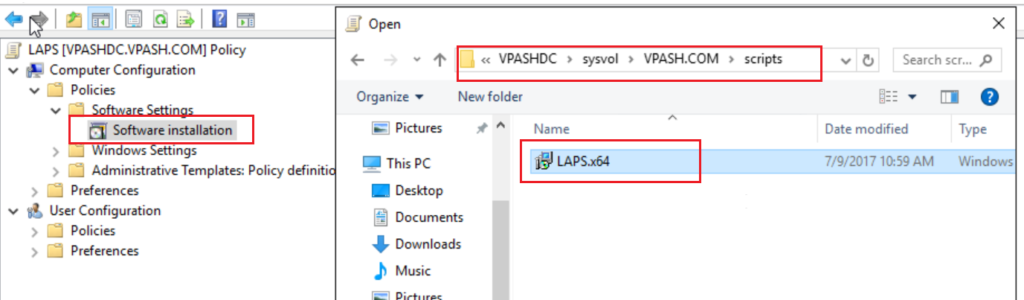
Deploy LAPS client in managed computers through GPO.
After that, the LAPS software will be pushed to control machines.
By default, this solution uses a password with maximum password complexity, 14 characters and changes the password every 30 days. You can change the values to suit your needs by editing a Group Policy.
You can change the individual password settings to fit your needs.
If you have decided to manage custom local Administrator account, you must specify its name in Group Policy.
If you do not want to allow setting planning password expiration of admin account for a longer time than maximum password age, you can do it in GPO:
Enable local admin password management
4- View the Local Admin Passwords for Controlled Machines.
You can do this from PowerShell with the following methods:
a. Command line:
We have applied policy on Server01 and excluded Server02
b. Or if we have the Fat client, we can launch that from:
c. Or as it’s an AD object attribute, you can view it on the Computers AD object.
To be continued in part 3
Thanks.